
How to Install and Use Gremlin on CentOS 7

Introduction
This tutorial will walkthrough how to install Gremlin on CentOS 7 and perform a Chaos Engineering experiment using a Gremlin CPU attack.
Prerequisites
Before you begin this tutorial, you'll need the following:
- A CentOS 7 server
- A Gremlin account
Create your Gremlin Free account
Step 1 - Getting Team Credentials
After you have created your Gremlin account, you will need to find your Gremlin Daemon credentials. Login to the Gremlin App using your Company name and sign-on credentials. These were emailed to you when you signed up to start using Gremlin.

Navigate to Team Settings from the user icon in the upper right hand corner.
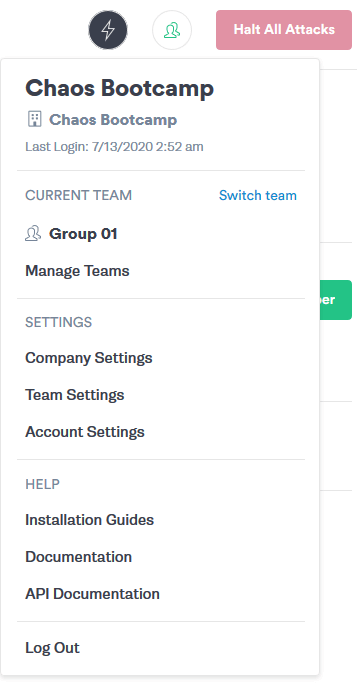
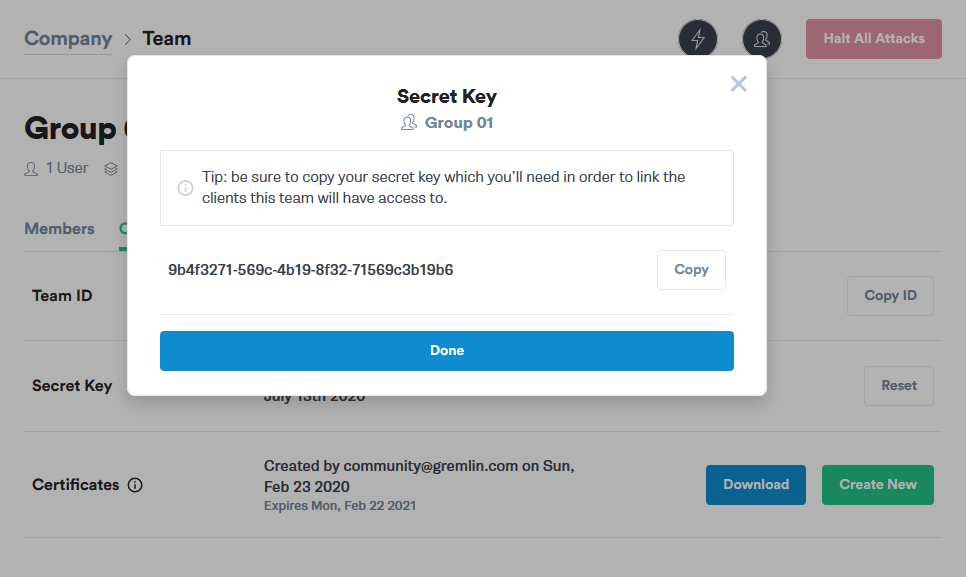
Click on the Configuration tab. Make a note of your Gremlin Team ID.

Press the Reset button next to Secret Key. A prompt will appear once the Secret Key has been set. Copy the key and keep it for future installation as this information will NOT be displayed again.
Step 2 - Installing the Gremlin Daemon and CLI
First, add the Gremlin RPM repository:
1# Add the Gremlin repo2sudo curl https://rpm.gremlin.com/gremlin.repo -o /etc/yum.repos.d/gremlin.repo
Then install the Gremlin daemon and CLI:
1# Install Gremlin client and daemon2sudo yum install -y gremlin gremlind
Then initialize Gremlin and follow the prompts:
1gremlin init2Please input your Team ID:31c485fb2-d288-5a7e-a6c3-070be181d66a4Please input your Team Secret:(Text output will not appear)56Using 1c485fb2-d288-5a7e-a6c3-070be181d66a for Team Id7Using 172.31.31.231 for Gremlin identifier
You are now ready to create attacks using the Gremlin App.
Step 3 - Creating attacks using the Gremlin App
You can use the Gremlin App or the Gremlin API to trigger Gremlin attacks. You can view the available range of Gremlin Attacks in Gremlin Help. For this example, we'll be focusing on the Gremlin App
To start an attack from the Gremlin App, select New Attack from the Attacks page.
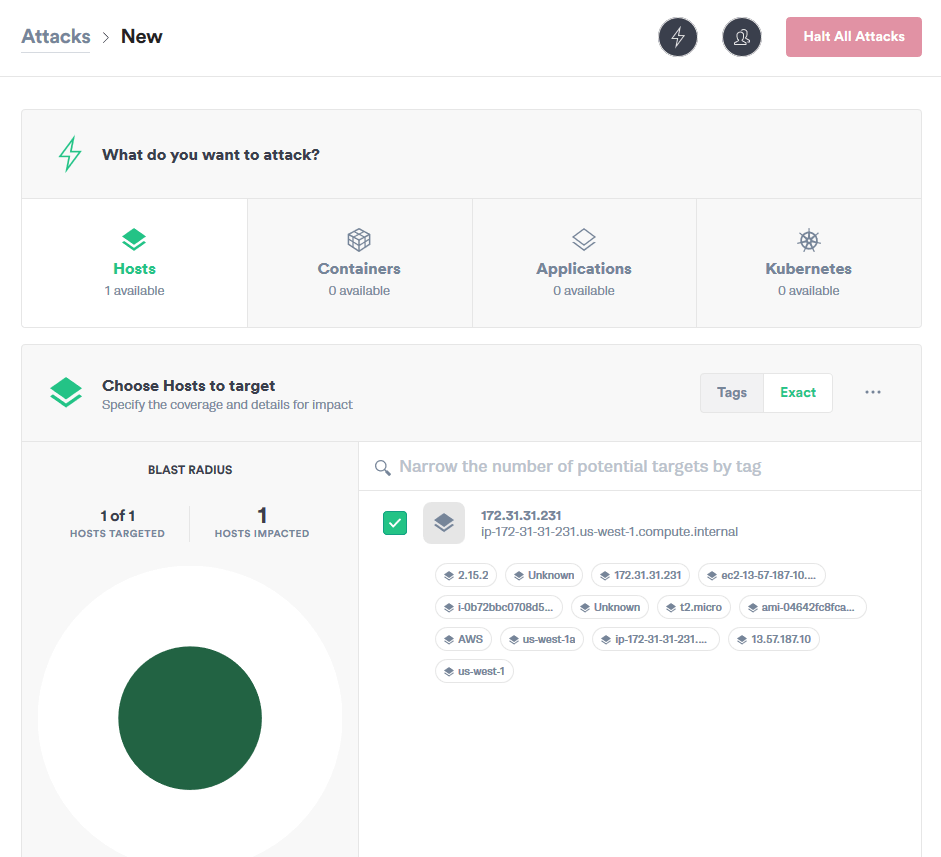
Under Choose Host to target, select Exact to select the specific host that we had set up in step 2. We know that this is the host because the IP matches from the last output of Gremlin init
The next step is Choose a Gremlin. It is here that we'll select the attack that we want to perform against the host.
The Hello World of Chaos Engineering is the CPU Resource Attack. Once we have set all the parameters of the attack, click Unleash Gremlin to start the attack.
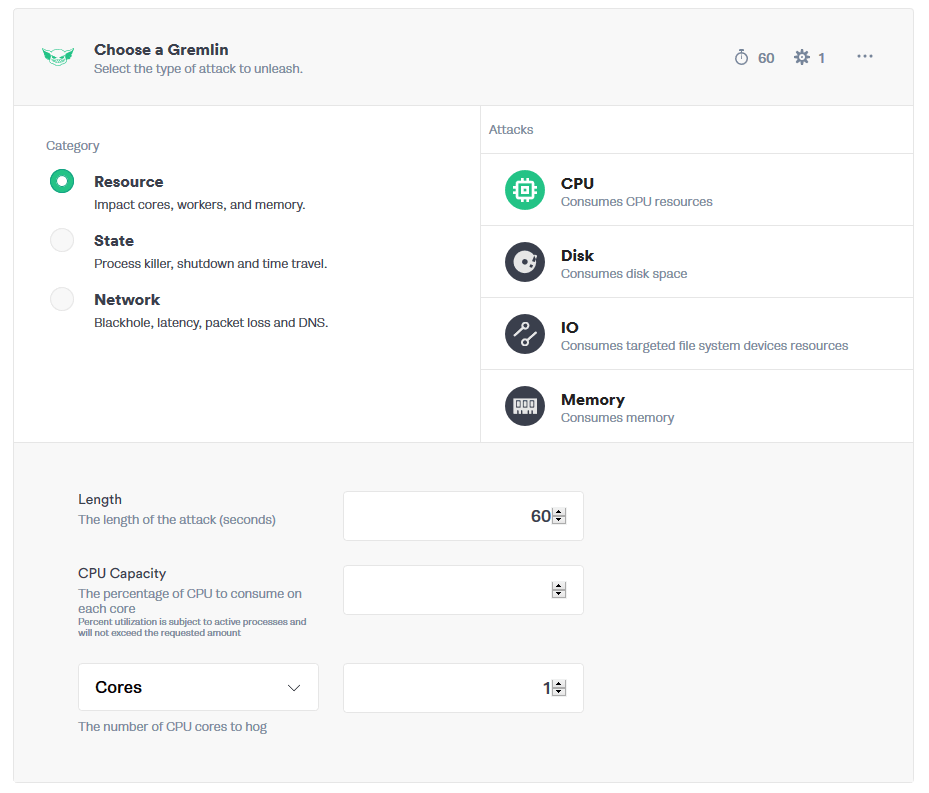
Your attack will begin to run, you will be able to view its progress via Gremlin Attacks in the Gremlin App.

On your server, run top to check the impact of the Gremlin Attack:
1top23top - 06:26:47 up 7 days, 7:00, 1 user, load average: 0.28, 0.07, 0.024Tasks: 105 total, 1 running, 104 sleeping, 0 stopped, 0 zombie5%Cpu(s): 79.7 us, 20.3 sy, 0.0 ni, 0.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st6KiB Mem : 1016120 total, 127140 free, 93956 used, 795024 buff/cache7KiB Swap: 0 total, 0 free, 0 used. 712192 avail Mem89 PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND1023768 gremlin 20 0 13268 11136 3576 S 99.3 1.1 0:14.05 gremlin1123766 root 20 0 40388 3600 3072 R 0.3 0.4 0:00.03 top12 1 root 20 0 37760 5760 3940 S 0.0 0.6 0:13.74 systemd13 2 root 20 0 0 0 0 S 0.0 0.0 0:00.00 kthreadd14 3 root 20 0 0 0 0 S 0.0 0.0 0:01.28 ksoftirqd/015 5 root 0 -20 0 0 0 S 0.0 0.0 0:00.00 kworker/0:0H16 7 root 20 0 0 0 0 S 0.0 0.0 0:06.14 rcu_sched17 8 root 20 0 0 0 0 S 0.0 0.0 0:00.00 rcu_bh18 9 root rt 0 0 0 0 S 0.0 0.0 0:00.00 migration/019 10 root rt 0 0 0 0 S 0.0 0.0 0:04.09 watchdog/0
When your attack is complete it will move to Completed Attacks.

Step 4 - Halting a CPU resource attack using the Gremlin App
You can stop a Gremlin Attack at anytime using the Gremlin App. Navigate to Gremlin Attacks and click on the halt button.
Conclusion
You've installed Gremlin on a server running CentOS 7 and validated that Gremlin works by running the Hello World of Chaos Engineering, the CPU Resource attack. You now possess tools that make it possible for you to explore additional Gremlin Attacks including attacks that impact State and Network.
Gremlin's Developer Guide is a great resource and reference for using Gremlin to do Chaos Engineering. You can also explore the Gremlin Blog for more information on how to use Chaos Engineering with your application infrastructure.
Related



Avoid downtime. Use Gremlin to turn failure into resilience.
Gremlin empowers you to proactively root out failure before it causes downtime. See how you can harness chaos to build resilient systems by requesting a demo of Gremlin.
Get started